Posts
How I automate patching desktops
It takes a long time to setup but worth it, computers should
not get policies they don’t need, at some point things will start stuffing up. I
have split desktops into 3 categories that suit our environment. Pilot get updates straight away and will reboot at night. Prod and PUC get updates 7 days later and have different reboot requirements.
|
Group |
Deadline |
User notifications |
Deadline behaviour outside maintenance window |
Device restart behaviour |
|
Pilot |
Asap |
All |
SW Updates Install |
Yes |
|
Prod |
7 days |
None |
SW Updates Install |
Suppressed |
|
PUC (Public Use computers such as Labs) |
7 days |
None |
SW Updates Install |
Yes |
I then split these groups into collections based on OS or
Office version requirements, so we have Office 2007, Office 2010, Office 2013,
Windows XP, Windows 7 x86, Windows 7 x64, Windows 8 x64.
A Pilot, PUC and PROD collection should be made so you can
limit the collections with it. These collections will vary in your environment.
Based on that you should have 21 collections - see ‘rules
and queries’ at the end for the messy queries
|
SUM-WORKSTATIONS-PROD–Office 2007 |
SUM-WORKSTATIONS-PROD–Office 2010 |
SUM-WORKSTATIONS-PROD–Office 2013 |
SUM-WORKSTATIONS-PROD–Windows XP |
|
SUM-WORKSTATIONS-PROD–Windows 7 x86 |
SUM-WORKSTATIONS-PROD–Windows 7 x64 |
SUM-WORKSTATIONS-PROD–Windows 8 x64 |
|
|
SUM-WORKSTATIONS-PILOT–Office 2007 |
SUM-WORKSTATIONS- PILOT–Office 2010 |
SUM-WORKSTATIONS- PILOT–Office 2013 |
SUM-WORKSTATIONS- PILOT–Windows XP |
|
SUM-WORKSTATIONS- PILOT–Windows 7 x86 |
SUM-WORKSTATIONS- PILOT–Windows 7 x64 |
SUM-WORKSTATIONS- PILOT–Windows 8 x64 |
|
|
SUM-WORKSTATIONS-PUC–Office 2007 |
SUM-WORKSTATIONS- PUC–Office 2010 |
SUM-WORKSTATIONS- PUC–Office 2013 |
SUM-WORKSTATIONS- PUC–Windows XP |
|
SUM-WORKSTATIONS- PUC –Windows 7 x86 |
SUM-WORKSTATIONS- PUC–Windows 7 x64 |
SUM-WORKSTATIONS- PUC–Windows 8 x64 |
Update:
Limit your pilot collections to a group of user's primary computers using this collection query
[code language="sql"]
Select SMS_R_SYSTEM.ResourceID,SMS_R_SYSTEM.ResourceType,SMS_R_SYSTEM.Name,SMS_R_SYSTEM.SMSUniqueIdentifier,SMS_R_SYSTEM.ResourceDomainORWorkgroup,SMS_R_SYSTEM.Client FROM SMS_R_System JOIN SMS_UserMachineRelationship ON SMS_R_System.Name=SMS_UserMachineRelationship.ResourceName JOIN SMS_R_User ON SMS_UserMachineRelationship.UniqueUserName=SMS_R_User.UniqueUserName WHERE SMS_UserMachineRelationship.Types=1 AND SMS_R_User.UserGroupName="DOMAIN\SCCM Software Updates Pilot User Group"
[/code]
Thanks Powersheller
Next you create a Software Update Group (the current
baseline of approved updates) for each Office/OS Version and a deployments for
each based on the rules from the first table.
Then you create Automatic Deployment rules for each
collection based (to run on Patch Tuesday/Wednesday Australia time) on the
rules from above and what type updates you want released in the last 3 weeks. They should be set to create a new software update group each time. See ‘rules and queries’ for what I have used.
You can also create an EndPoint Protection definitions ADR, however that should be set to use the existing software update group as the updates always superseed each time.
Rules and Queries:
|
Query Name |
Query |
|
Office 2007 |
See attachment |
|
Office 2010 |
See attachment |
|
Office 2013 |
See attachment |
|
Windows XP |
See attachment |
|
Windows 7 x86 |
See attachment |
|
Windows 7 x64 |
See attachment |
|
Windows 8 x64 |
See attachment |
|
Rule Name |
Rules |
|
Office 2007 |
Date Released or revised: Last 3 weeks Product: “Office 2007” Title: 32-Bit Update Classification: “Critical Updates” OR “Security Updates” OR |
|
Office 2010 |
Date Released or revised: Last 3 weeks Product: “Office 2010” Title: 32-Bit Update Classification: “Critical Updates” OR “Security Updates” OR |
|
Office 2013 |
Date Released or revised: Last 3 weeks Product: “Office 2013” Title: 32-Bit Update Classification: “Critical Updates” OR “Security Updates” OR |
|
Windows 7 x86 |
Date Released or revised: Last 3 weeks Product: “Windows 7” Title: -x64 Update Classification: “Critical Updates” OR “Security Updates” OR |
|
Windows 7 x64 |
Date Released or revised: Last 3 weeks Product: “Windows 7” Title: x64 Update Classification: “Critical Updates” OR “Security Updates” OR |
|
Windows 8 x64 |
Date Released or revised: Last 3 weeks Product: “Windows 8” OR “Windows 8.1” Title: x64 Update Classification: “Critical Updates” OR “Security Updates” OR |
OSD Black screen of death.
After using a new captured image (Win 7 x64) certain machines were not completing OSD and ending up at a black screen with just a mouse cursor.
Dell T1700, E6440, E7240, M4800. This was after the May patching, the only update that has been reported to play up (well with flash?) was KB2926765. We removed this patch from the base and the problem no longer occured. It's possible that it affects machines with the nic I217-LM, but probably a revision as it did not happen on the 9020.
Update: I think it is to do with driver injection and i7 cpu's. We still had some issues after this with drivers not installing correctly on i7's. Using the x64 boot wim resolved this.
Would love to hear if anyone else encounters this.
Single Functioning Software updates
We get to package WinZip every version, and it got me thinking they could have probably stopped at maybe version 2 or well when they added Rar and Iso support. It seems they started adding random stuff to it around version 8. http://en.wikipedia.org/wiki/WinZip#History
One version they decided to add a feature that deleted files on USB drives.
I like that they skipped 13. I think they can stop now, adding a zip to cloud won't make using files any easier!
WinDVD, I don't know much about this software however their developers must be running out of things to do, when the installer is this bright blue 3d spaceship thingy that almost crashes my machine and downloads itself it makes me think they are running out of things to do as well.
Flash - Needs to go away, not sure what they can add to it however they could make their installer more enterprise friendly.
Dropbox - Is one of my favorite apps, hope it doesn't go to silly. Maybe they will add cloud to zip, take that WinZIp!
Powershell script to clean up IIS's log file mess
Management Point's rely heavily on IIS and IIS loves to log a lot which will fill up your hard drive. Here's a script that deletes logs older than 14 days. Location and amount of days can be changed easily.
We have ours scheduled to run monthly on site systems using IIS.
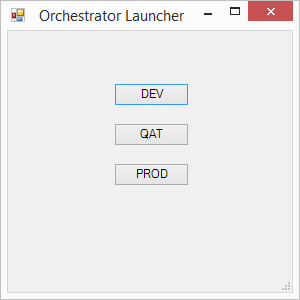
Orchestrator RunBook Designer Launcher!
Unfortunately Orchestrator only remembers the last server you connected to.
I got sick of having to type in different servers for DEV, QAT and PROD so I created a nice GUI with powershell to launch each environment.
Source code and PowerShell Studio file download OrchestratorLauncher.zip
It edit's the XML config file then launches the runbook designer. You would need to change the $FilePath if you are running Windows x86.
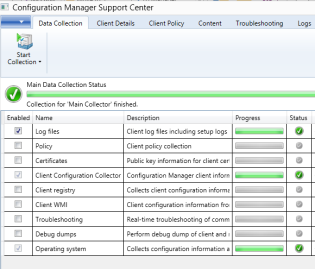
Microsoft Configuration Manager Support Center
Have you ever needed someone to collect logs off a machine and came to find that the vital log you wanted wasn't collected? Lost in the sea of logs?
Microsoft feels your pain!
Microsoft has released an excellent support tool to assist in troubleshooting ConfigMgr. It can collect logs, policys, wmi, registry etc; from remote or local machines. Also includes a log viewer that groups logs by function. I think it will eventually replace CMTrace.
It's in BETA so read the release notes! Update: It's released!
http://www.microsoft.com/en-us/download/details.aspx?id=42645
Multicast website component is not installed on Https DPs
We recently logged a case with Microsoft as multicast wasn't working because the SMS_MCS_AltAuth IIS virtual directory was missing. The work around is to delete the condition in the msi (SMSbinx64mcs.msi)
MCSIsapiAltAuth.866DCF8D_BC89_48AE_9AE6_69F1BAAEF805 in the MSI:
(SMSSSLSTATE >< 1)
and then enable multicast.
This is due to the MSI evaluating whether the site is HTTPS instead of the component.
This has been fixed in R2.