logfiles
Monitoring your fleets event logs - Part 2
Install Splunk - It's free! https://www.splunk.com/en_us/download/splunk-enterprise.html
Modify Program Files\Splunk\etc\system\local\inputs.conf
Add the lines
[WinEventLog]
evt_resolve_ad_obj = 1
Then we need to reboot splunk, in Splunk click Settings, then Server controls and click Restart Splunk
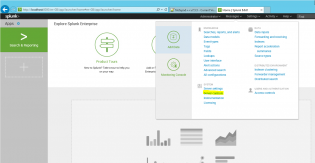
Next we need to add our data source, click Add Data from the launch screen, then monitor
Choose Local Events then ForwardedEvents and click Next
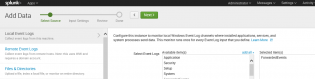
Click Create a new index, call it ForwardedEvents, click Save, change the Index to ForwardedEvents and then click Review, Submit
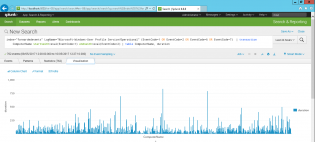
Give it some time to collect a few logins, then go to Search & Reporting
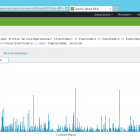
index="forwardedevents" LogName="Microsoft-Windows-User Profile Service/Operational" (EventCode=1 OR EventCode=2 OR EventCode=6 OR EventCode=7) | transaction ComputerName startswith=eval(EventCode=1) endswith=eval(EventCode=2) | table ComputerName, duration
So I'm using the selected data, filtering for 4 event codes, then getting the time between event code 1 and 2, and putting it into a table..
Edit: This search can be a bit funny, the delay ended up being between synching the roaming profile so I've also ran
index="forwardedevents" LogName="Microsoft-Windows-User Profile Service/Operational" (EventCode=1 OR EventCode=2 OR EventCode=6 OR EventCode=7) | transaction ComputerName startswith=eval(EventCode=6) endswith=eval(EventCode=7) | table ComputerName, duration
Then click on the Visualization tab
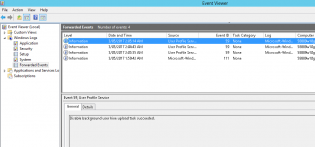
This also lets you dive into each login by clicking one and get the event logs!
You can save this as a report, dashboard and share with people.
There is so much more you can do with this software, and it takes some time to learn it. Will post more as I do..
Monitoring your fleets event logs - Part 1
Windows has an amazing feature that let's you collect logs from remote computers, it's called Windows Event forwarding and is pretty easy to set up. Once we have this data we can use free tools such as Splunk or GrayLog to analyse the data, find patterns, fix.
Below is the way to get started collecting the user profile logs to analyse things such as login performance with roaming profiles, something we are dealing with right now! Please note you need to enable winrm on your computers for forwarding to work.
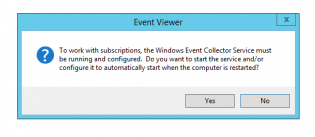
First you need a machine that will be the data collectior.
- On that machine open Event Viewer and right click Subscriptions. You may get the following message to enable the service on startup
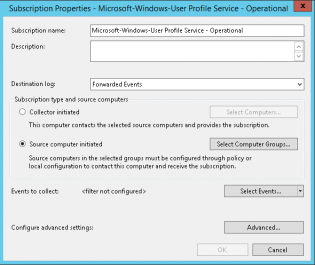
2. Now you should only collect data that you will use, in this example we are collecting the Microsoft-Windows-User Profile Service/Operational events so we will call it Microsoft-Windows-User Profile Service - Operational
3. Change the type to Source computer initiated and click Select Computer Groups
4. Add the group of machines to the Computer list and click OK
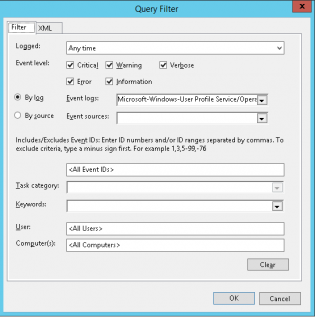
5. Click Select Events
6. We now select the Applications and Services Logs\Microsoft\Windows\User Profile Service
7. You can configure advanced settings to control how the computers forward the events.
8. Click OK
9. To get clean data we need to change the format of returned events by running the command:
wecutil ss "Microsoft-Windows-User Profile Service - Operational" /cf:Events
10. Next you deploy a group policy that tells your computers to go to the data collector for jobs
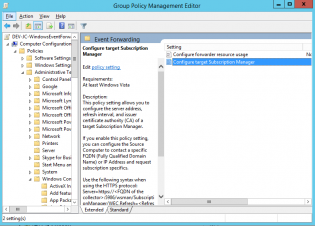
Create a group policy using Computer Configuration\Policies\Administrative Templates\Windows Components\Event Forwarding
11. Select Configure target Subscription Manager
12. Set to Enabled
13. Click Show
14. Insert the line
Server=http://SERVER.FQDN:5985/wsman/SubscriptionManager/WEC,Refresh=60
15. Replace SERVER.FQDN with your data collector's name.
16. To test run GPUPDATE /FORCE on the remote machine
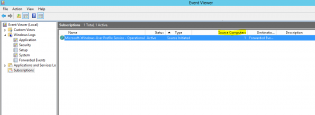
17. If successful, on the data machine you will see the number of source computers change and logs in the forwarded events
Visit https://blogs.technet.microsoft.com/jepayne/2015/11/23/monitoring-what-matters-windows-event-forwarding-for-everyone-even-if-you-already-have-a-siem/ for more information.
PART 2
Application Catalog logs
There are 2 operational logs for the App Catalog server side.
- <Drive Letter>SMS_CCMCMApplicationCatalogLogsServicePortalWebSite.log
- <Drive Letter>SMS_CCMCMApplicationCatalogSvcLogsServicePortalWebService.log
Troubleshooting
If the App catalog has an error message "Cannot Connect to the Application Server" this is referring the to the ServicePortalWebService.log.
So far I have only seen the error:
error: WriteHeadersCallback(WebExceptionStatus errorStatus, ConnectStream stream, Boolean async)
in the log ServicePortalWebSite.log
restarting the IIS service resolved this.
Powershell script to clean up IIS's log file mess
Management Point's rely heavily on IIS and IIS loves to log a lot which will fill up your hard drive. Here's a script that deletes logs older than 14 days. Location and amount of days can be changed easily.
We have ours scheduled to run monthly on site systems using IIS.