KB2918614 - UAC GATE
Update 13/11:
A new hotfix was released:
http://support.microsoft.com/kb/3008627
After install above hotfix, you can use below registry key manually as a switch to enable or disable the UAC :
Under Key “HKLMSOFTWAREPoliciesMicrosoftWindowsInstaller”, create a DWORD: “NoUACforHashMissing” and set its Value to 1.
Update 17/09:
You can whitelist existing msi's. Not tested yet, will test and deploy as a dependency for the update.
https://send.estate/s?e=8d19fef3f12531a
After further discussion with our product team. They provided us a new workaround that you can add the existing applications into a whitelist. Here is the details:
Whitelisting: If you trust the application that it is always digitally signed and does not contain any malicious payload, add it to the whitelist.
There are two REG keys needed for whitelisting:
1) Need Whitelisting: Under Key “HKLMSOFTWAREPoliciesMicrosoftWindowsInstaller”, create a DWORD: “SecureRepairPolicy” and set its Value to 2.
We (Microsoft) wrote a script to add the white list for customer automatically. Please download the attachment from https://send.estate/s?e=8d19fef3f12531a and rename it as .vbs. Double clicking it will help to add the whitelist for all of the installed MSI application.
Update on KB2918614.
Microsoft:
This security update resolves a privately disclosed vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker runs a specially crafted application that attempts to repair a previously-installed application. An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability.
Workaround if you have problems with repairing application:
==================================================
1. Uninstall the application and reinstall it with the security update installed. (sourcehash file generated with security update)2. Manually copy the sourcehash file to c:windowsinstaller folder. As the sourcehash file is generated based on the application files, the sourcehash file generated on computer A can be used on computer B.
Another Workaround:
Not sure of the consequences fully yet - Remove
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionInstallerUserDataS-1-5-18Products{guid}InstallPropertiesLocalPackage
This then uses Windows Installer Source list for msi repair without promtping. And generates you a fresh sourcehash.
Uninstall Commands (via SCCM Package):
Windows 7 x64 Uninstall: c:windowssysnativecmd.exe /c dism.exe /online /remove-package /PackageName:"Package_for_KB2918614~31bf3856ad364e35~amd64~~6.1.1.4" /quiet /norestart
Windows 8 x64 Uninstall: c:windowssysnativecmd.exe /c dism.exe /online /remove-package /PackageName:"Package_for_KB2918614~31bf3856ad364e35~amd64~~6.3.1.4" /quiet /norestart
Windows 2008 R2 x64 Uninstall: c:windowssysnativecmd.exe /c dism.exe /online /remove-package /PackageName:"Package_for_KB2918614~31bf3856ad364e35~amd64~~6.1.1.4" /quiet /norestart
Sysnative is required otherwise you get error 11.
Windows 7 x86 Uninstall: cmd.exe /c dism.exe /online /remove-package /PackageName:"Package_for_KB2918614~31bf3856ad364e35~x86~~6.1.1.4" /quiet /norestart
The work arounds aren't that easy when you have over a 1000 apps, the update would be ok in your base image.
Thanks to Jörgen Nilsson for discovering this via http://ccmexec.com/2014/09/kb2918614-windows-installer-triggers-uac/
5 Comments
Trackbacks for this post
-
[…] to HappySCCM https://happysccm.com//kb2918614-uac-gate/ who have posted the answer from Microsoft and a valid […]

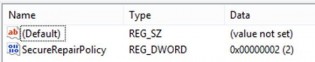
Thanks for sharing.
Whitelisting works perfect for us on Win7 and Win8.1.
Thank you very much for sharing....
Where you say "We (Microsoft) wrote a script to add the white list for customer automatically. Please download the attachment and rename it as .vbs"
I can't see the attachment you are referring to ..... (??)
Hi Wayne, updated the post, link was above, it makes more sense to put it within the sentence.